Purple Team
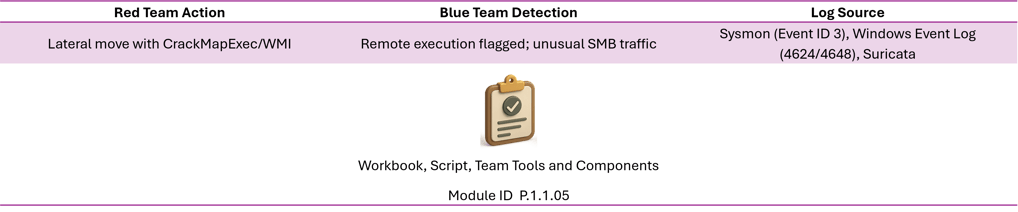
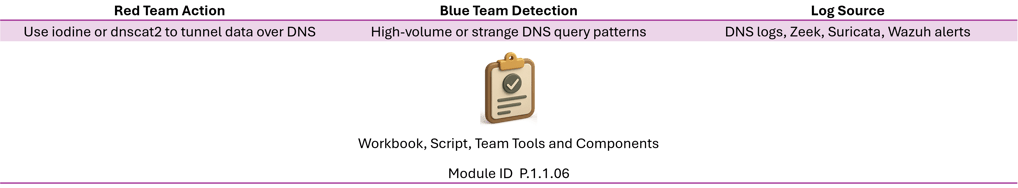
Here are Purple Team validation use cases — scenarios where Red Team tactics are directly used to test or validate Blue Team defenses (SIEM, IDS/IPS, EDR, etc). Each use case includes the Red Team action, the expected Blue Team detection, and the log/artifact source




Credential Dumping (LSASS Access)


Brute-Force Login Attack


Phishing + Payload Execution


Suspicious PowerShell (Living off the Land)


Lateral Movement (WMI, PsExec)


DNS Tunneling


Reverse Shell via HTTP/S


Malware Dropper Detection


Command & Control (C2) Persistence


Data Exfiltration over HTTPS


Purple Team Playbook