Black Team
From consulting and strategy development to implementation and support, our comprehensive services can help your business thrive.


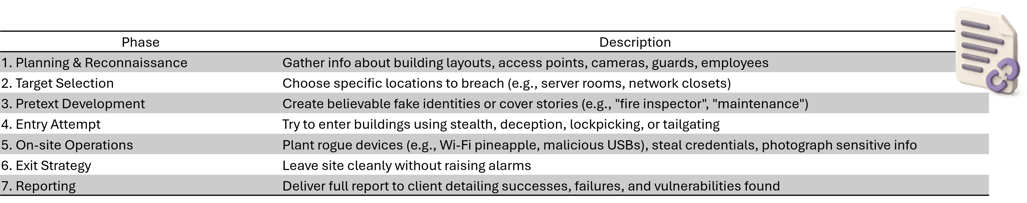
🏢 Physical Access Testing
Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
💻 Rogue Device Detection
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates
Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
👤 Insider Threat Simulation
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates









Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
🎣 Social Engineering Tests
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates












Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
🔌 Device Forensics / EDR Awareness
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates












Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
🪪 ID Cloning / Access Badge Testing
Objective: Test user curiosity and policy compliance
Execution:
Drop USBs labeled “HR_Payroll_2025”, “Confidential”, “Photos” in break rooms, lobbies, or bathrooms
USB launches payload or logs execution
Required Toolkit:
Tool
Role
Rubber Ducky / MalDuino
Auto-run malicious payload (PowerShell, keylogger)
Travis/Truffle Security USB
Tamper-proof monitoring USB
🎣 Malicious USB Drop
Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
🛜 Plug-and-Play Attack
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates












Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
📸 Unauthorized Surveillance
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates












Beginner
Host Discovery
Port Scanning
Service Version Detection
OS Fingerprinting
Quick Scan
Advanced
Our architecture services prioritize function and form to create spaces that stand the test of time.
🚷 Red Team Physical Lockout
Beginner
SYN Scan (Stealth)
UDP Scan
Idle Scan (Zombie)
Fragment Packets
Timing Templates